How do you securely and safely store your password for your password manager? Password managers solve the problem of storing the basket of passwords to be used for each application, but how should the master password for the password manager be saved? If this password is to be stored in an online digital medium, then obviously that medium will need to be password protected, since the security for the basket of passwords is only as good as the security into this online digital medium. But where should the keys to the online digital medium be stored? If the logic is followed through to the end, then in my humble opinion, the root password should be stored offline.
If the root password should be stored offline, should it just be committed to memory? This would not work for me since I have a tendency of forgetting strong passwords, and it would be quite a disaster to lose access to the basket of passwords. Thus, I argue that the root password should be written down but stored securely away from prying eyes of course. However, how does one protect against loss of an offline key by disasters such as fires? The idea is to mark the key on a high-temperature resistant medium, but paranoid infosec aficionados surely would not want to outsource the fabrication of the marked medium to an untrusted or trusted 3rd party. The ultimate solution is then to mark your own keys into a stainless steel medium.
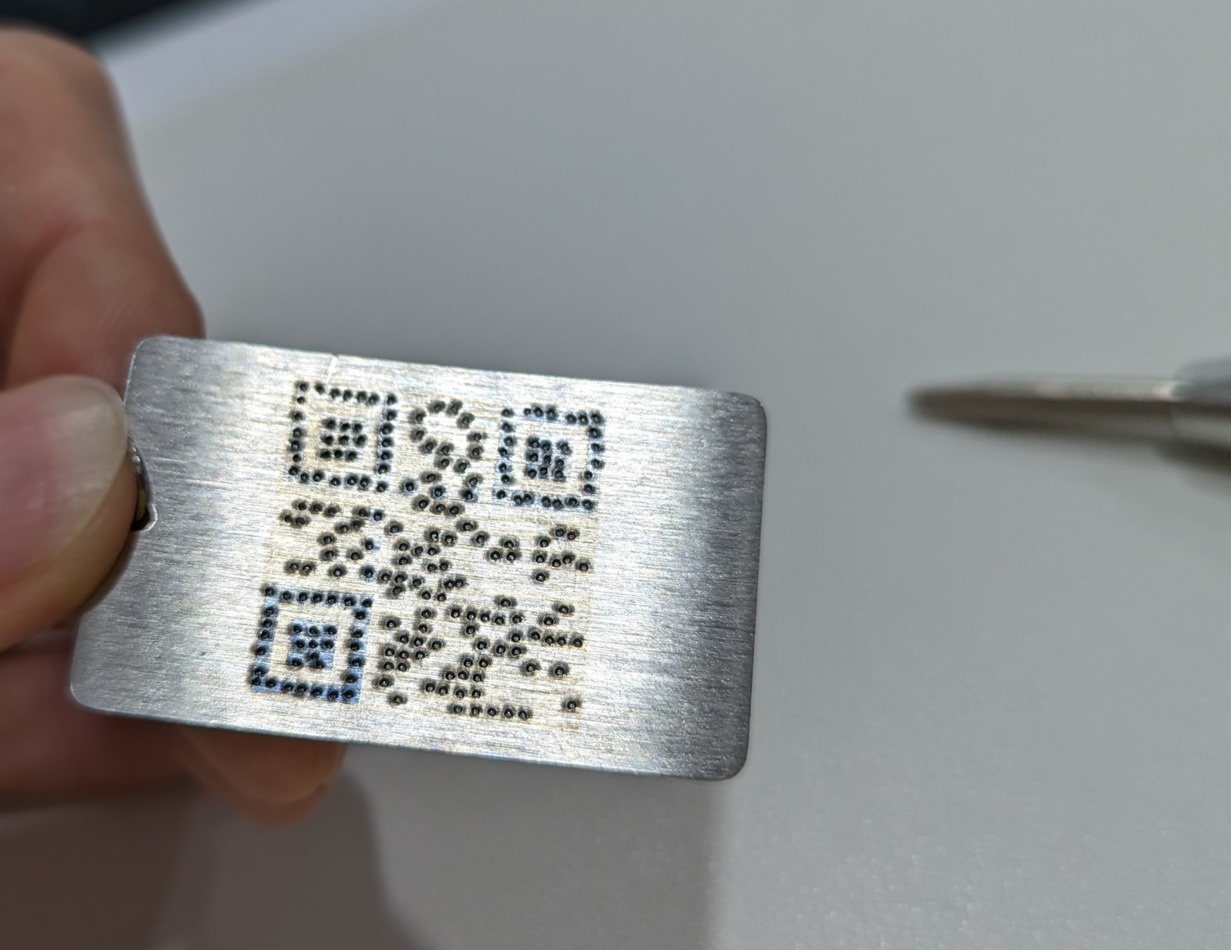
Here, I demonstrate how to mark a QR encoded ascii key into a stainless steel keychain. The basic blocks of the QR code were laser engraved into a keychain by a third party since the basic blocks contain no data, but only alignment marks, versioning and timing information.

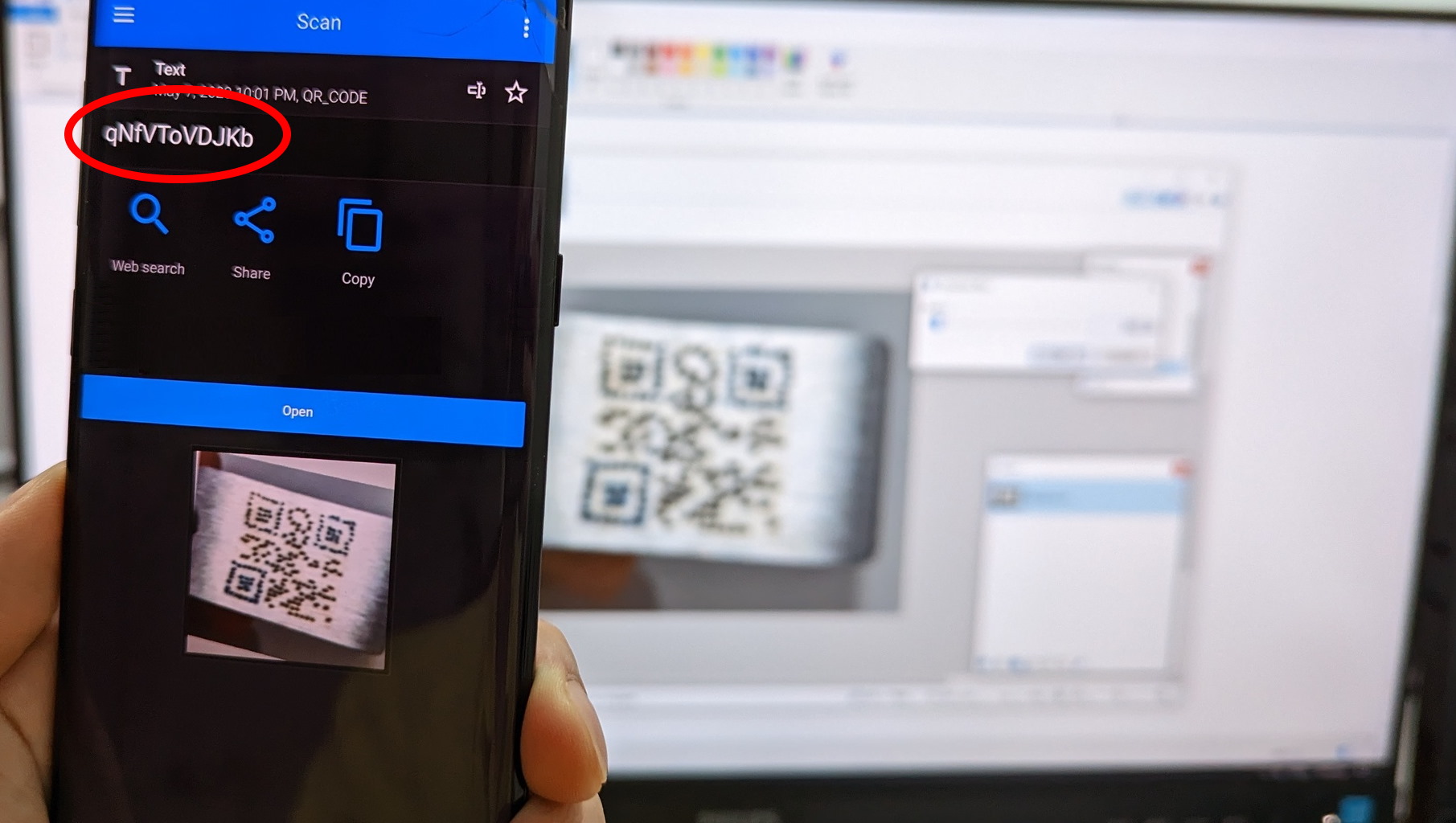
The ascii key qNfVToVDJKb was randomly generated and converted into a QR code, then punched one bit at a time into the stainless steel keychain with a spring-loaded center punch.

Since the laser-engraved template already contains bits that are always marked, i.e the alignment marks and timing information, they can be laser engraved directly to save the effort of punching these bits. However, it is good to just punch them anyway since the mechanically-deformed holes should be able to last longer than the laser marks affecting only the surfaces of the keychain.

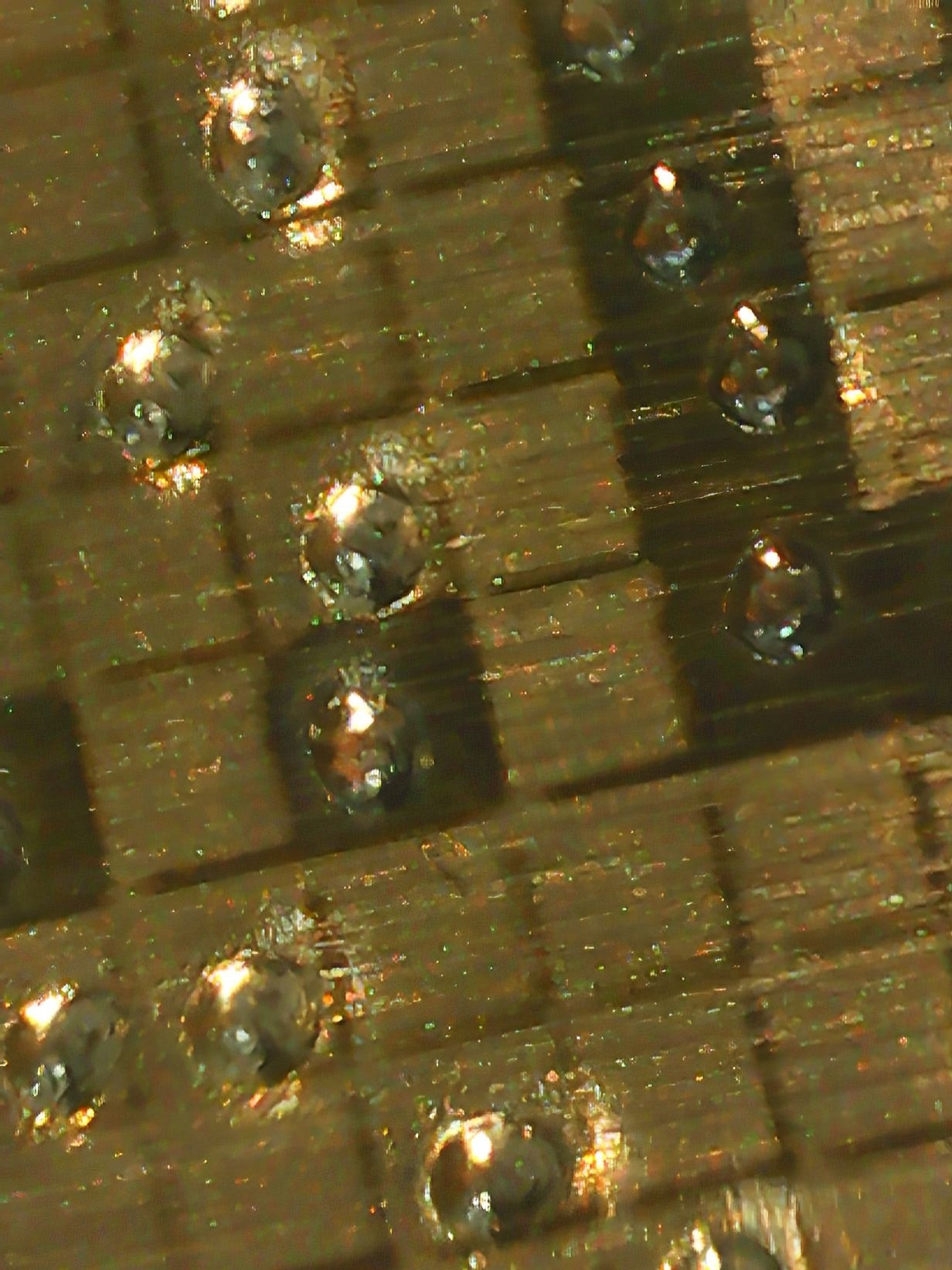
When observed under a microscope, the punched bits appear as clear depressions. Even in some unforeseeable disaster where this tag is badly mangled or perhaps charred too severely, the depressions are likely to remain visible when observed at a microscopic level for recovery.
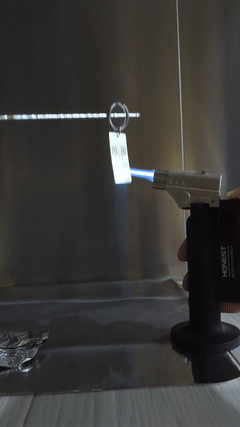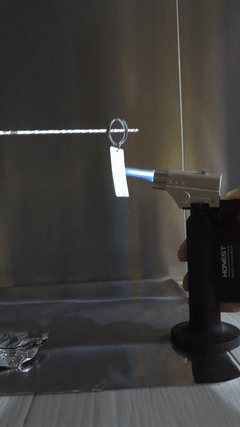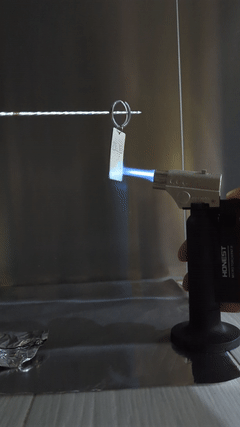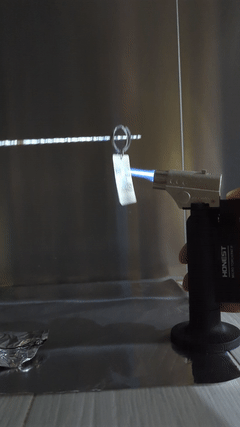
The keychain survives a fire since it was specifically chosen to be made of stainless steel. No damages are seen after the blowtorch exposure. A slight discoloration is observed but that does not affect the function of this keychain.
When scanned with a QR code reader, the tag takes some time to scan and is only successful under optimal lighting conditions and angle, but nonetheless scans and reproduces the original key in plaintext. In a scenario where a QR code decoder cannot decode the keys automatically, a human can help with this decoding by transcribing each bits to another graphic to recover the keys.
You are free to copy the ideas and make your own set, or I can get you the same set if you cover the costs. As for me, I shall discard this now-compromised key and possibly engrave actual keys into a second keychain.